OpenSSL Vulnerability
Update as of Nov 1, 2022
On Nov 1, 2022, OpenSSL released version 3.0.7 along with a blog post giving high level information about the vulnerabilities. It is important to note that two CVEs were announced and they have been rated High as opposed to Critical. Both CVEs are buffer overflow vulnerabilities that occur when parsing X.509 certificates.
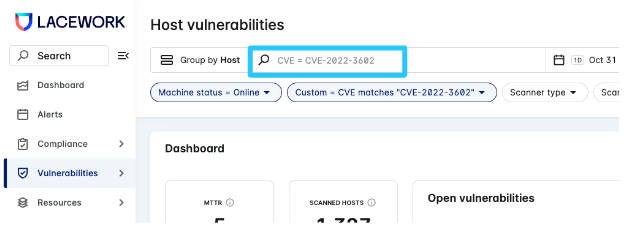
Update: For the most accurate results, going forward you should use CVE-2022-3602 and CVE-2022-3786 to identify and remediate vulnerabilities in your environment.
CVE Details
CVE-2022-3602 - Initially rated Critical and downgraded to High, this vulnerability is an off-by-one resulting in a four byte buffer overflow that occurs during X.509 certificate validation. A certificate with a maliciously crafted email address could result in remote code execution or, more likely, denial of service. Note that this occurs after certificate chain validation.
CVE-2022-3786 - This High severity vulnerability is a buffer overflow that allows an attacker to write an arbitrary number of “.”s outside an allocated buffer. A certificate with a maliciously crafted email address could theoretically result in remote code execution but realistically would result in a denial of service. Note that this also occurs after the certificate chain validation occurs.
How to Find these Vulnerabilities in Lacework
Search for these new CVEs in either the Container or Host Vulnerability pages.
Example:
Additional Resources
What is the Recommended Remediation?
Per the OpenSSL blog post, users of OpenSSL 3.0.0 - 3.0.6 are encouraged to upgrade to 3.0.7 as soon as possible. If you obtain your copy of OpenSSL from your operating system vendor or other third party, then you should obtain an updated version from them as soon as possible.
Update: The following guidance applies to the time period before Nov 1, 2022. For the most accurate results, going forward you should use CVE-2022-3602 and CVE-2022-3786 to identify and remediate vulnerabilities in your environment.
Prior to Nov 1, 2022
Overview
On Oct 25, 2022, OpenSSL announced a forthcoming release of OpenSSL version 3.0.7 to fix a critical vulnerability. The release and more information about the vulnerability will be available on Nov 1, 2022. This document describes how Lacework can help you find and remediate the vulnerability. We will continue to update this document as more information is released.
How to Find this Vulnerability in Lacework
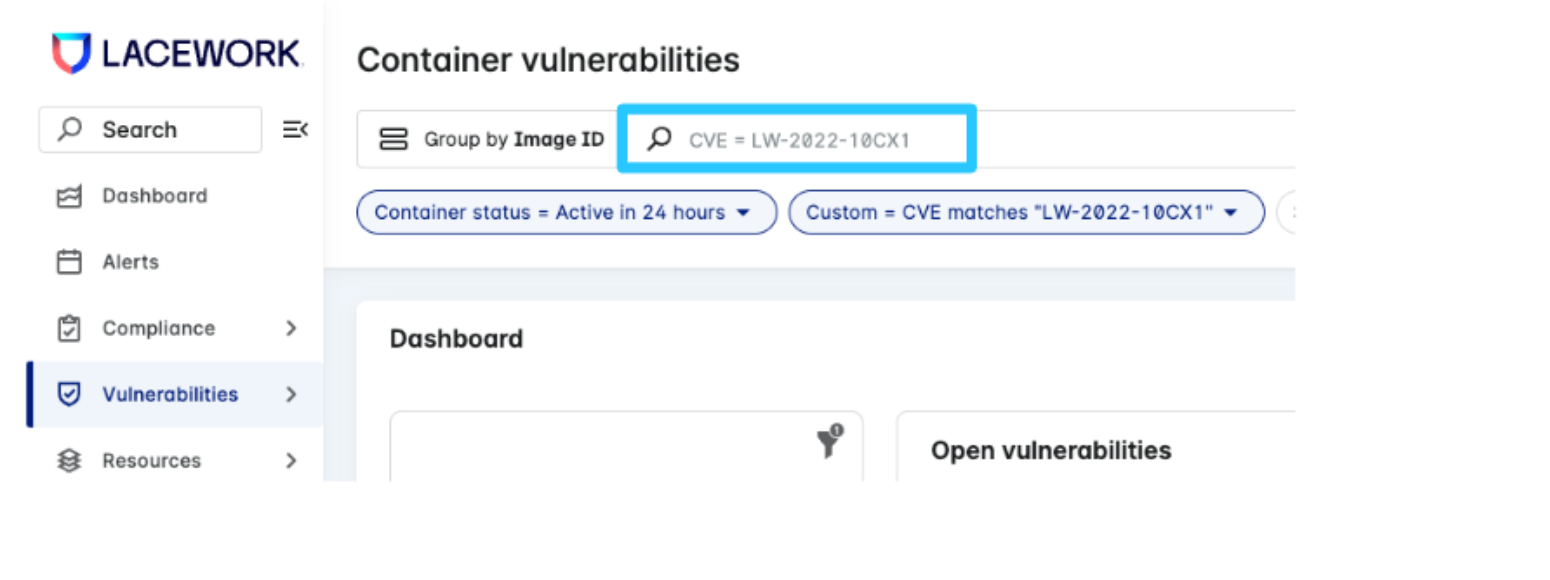
Because OpenSSL has not yet released the CVE identifier to the public, you can use the identifier LW-2022-10CX1 to find the most up-to-date vulnerability assessment from Lacework Labs. Search for LW-2022-10CX1 in either Host Vulnerabilities or Container Vulnerabilities, as you would any other CVE.
Example:
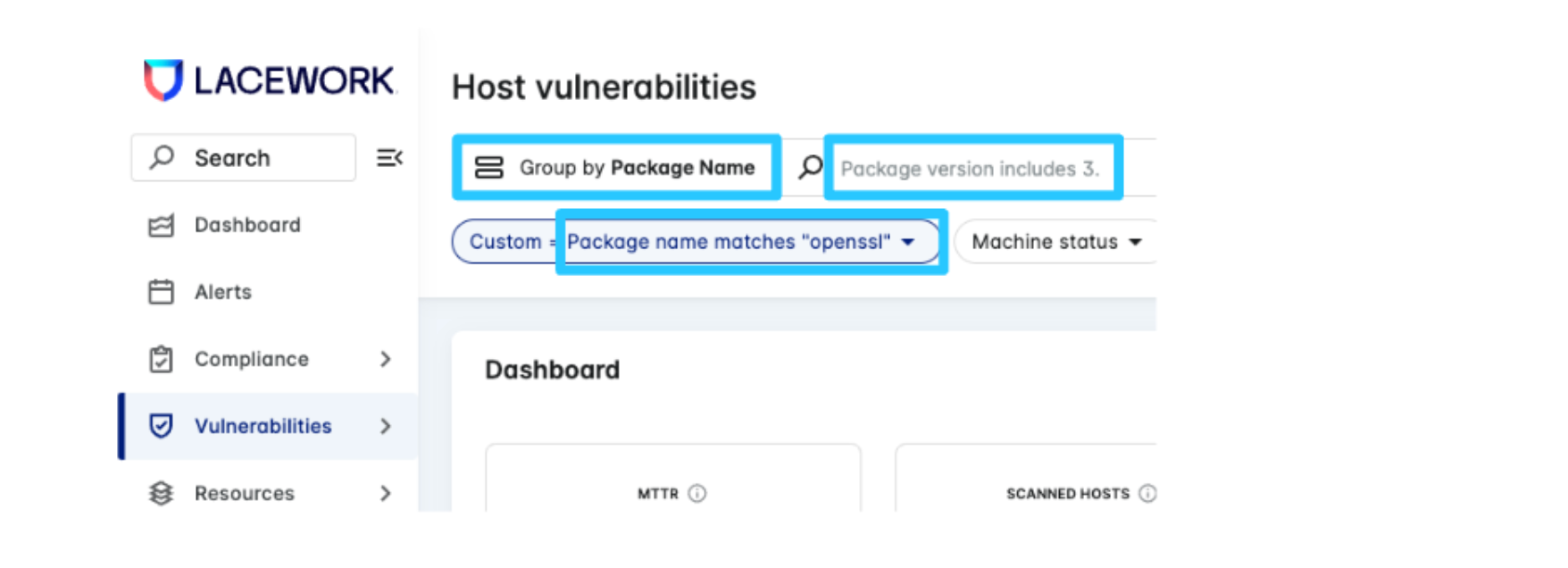
You can also search for the specific vulnerable package and version combinations using the Group by Package Name view.
Example:
Using the embedded download functionality, you can export a list of all hosts or container images that contain this vulnerability. The active filters influence which hosts/images are shown when using the Download CSV option. We recommend that you use them to only return the specified CVE for all hosts/images.
What is the Recommended Remediation?
It is critical that you upgrade OpenSSL to version 3.0.7 (expected release on November 1, 2022) as soon as possible to remediate this vulnerability.